安居客滑块验证码AES加密解析
网页链接:https://www.anjuke.com/captcha-verify/?callback=shield&from=antispam
请求接口:1.https://anjuke.com/captcha/getInfoTp
2.https://anjuke.com/captcha/checkInfoTp
加密参数:请求参数dInfo,响应参数info,请求参数data
请求接口分析
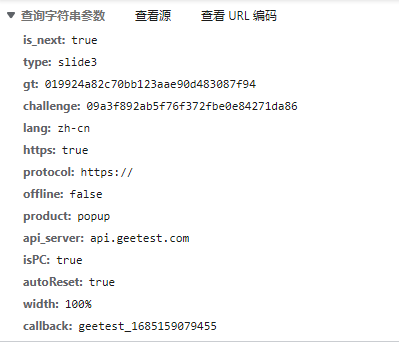
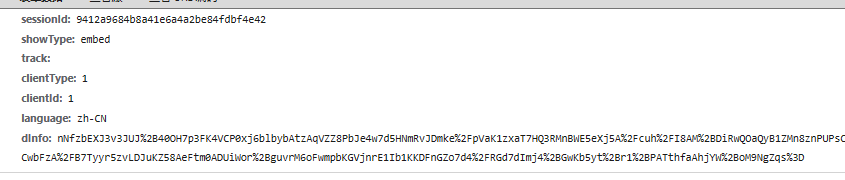
请求参数:
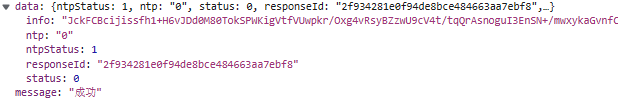
响应体:
sessionId通过搜索可以发现是隐藏在html里面
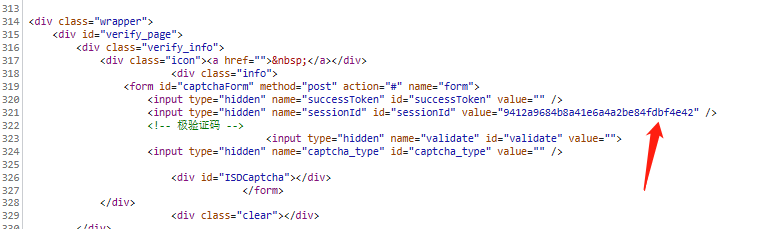
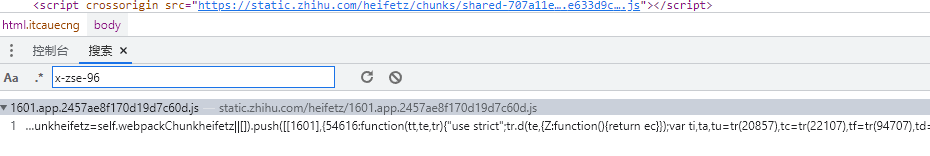
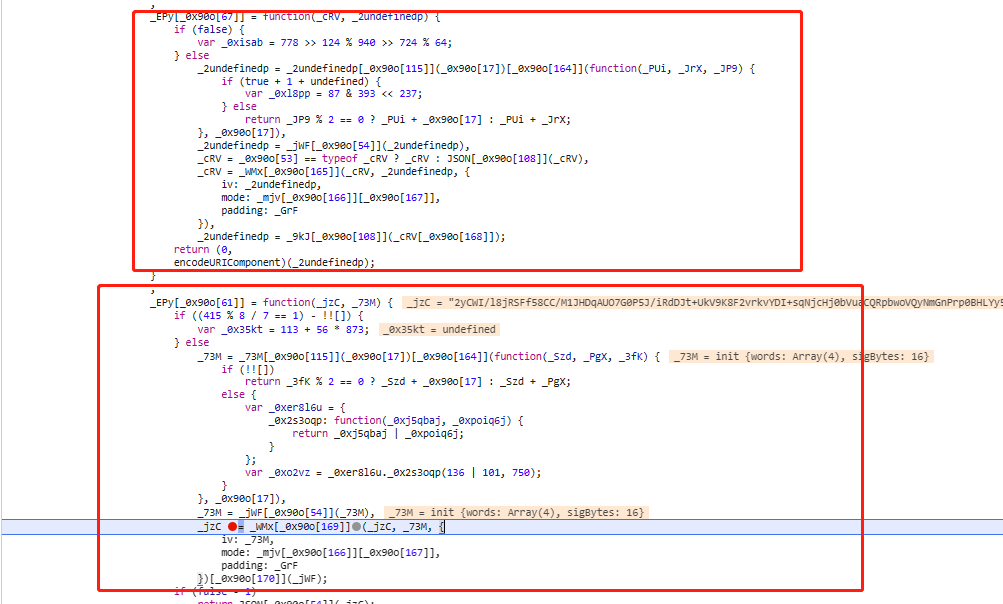
dinfo字段通过搜索,可以找到对应的加密方式
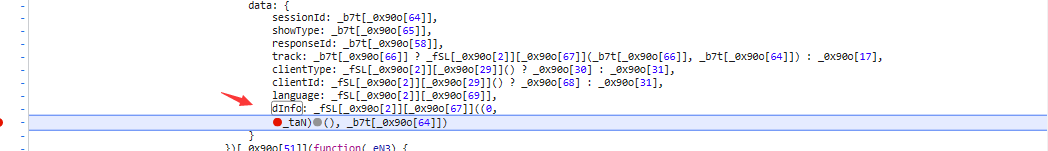
两个参数和对应的加密函数,一个是请求头信息,一个是sessionid,加密方式是AES的cbc模式,iv偏移值是获取sessionid的奇数位字符
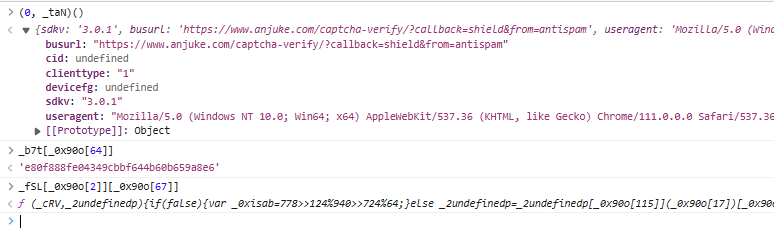
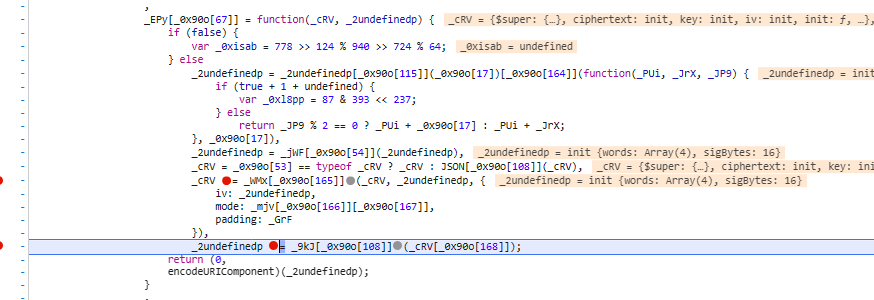
使用python的Crypto模块进行加密获取
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18from urllib.parse import quote_plus
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
session_id = html.xpath('//*[@id="sessionId"]/@value')[0]
iv = ""
for k, v in enumerate():
if k % 2 != 0:
iv += v
text = {
"sdkv": "3.0.1",
"busurl": "",
"useragent": "",
"clienttype": 1
}
cipher = AES.new(key=bytes(aes_key_iv, encoding='utf-8'), mode=AES.MODE_CBC, iv=bytes(aes_key_iv, encoding='utf-8'))
result = base64.b64encode(cipher.encrypt(pad(text.encode('utf-8'), 16))).decode('utf- 8')
result = quote_plus(result)对获取的响应体进行解析,猜测也是aes加密,打上断点查看,果然如此,传入的_jzC正是响应体,同样使用Crypto模块进行解密,这样我们就拿到了responseId和两张验证码的图片链接
1
2
3
4
5
6cipher = _AES.new(
key=bytes(aes_key, encoding='utf-8'),
mode=_AES.MODE_CBC,
iv=bytes(aes_key, encoding='utf-8')
)
result = unpad(cipher.decrypt(base64.b64decode(ciphertext)), 16).decode('utf-8')
验证码缺口位置解析
1.可以使用opencv和ddddocr模块进行解析,这里使用cv2对验证码图片进行处理,找出缺口位置
1 | |
轨迹处理
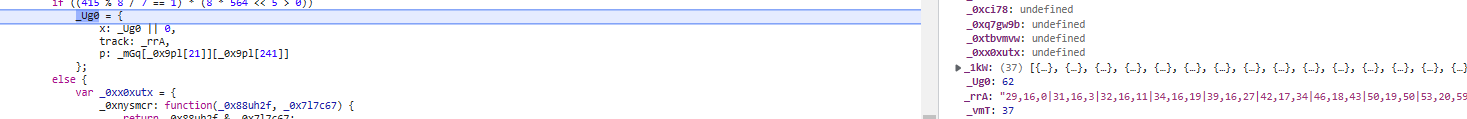
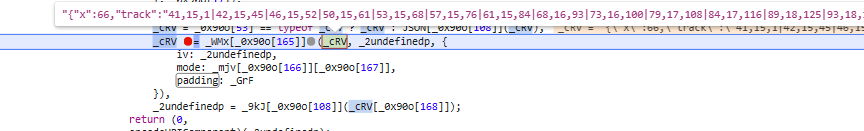
1.直接搜索track定位到轨迹加密的地方,_Ug0 由三个参数组成,x 是水平滑动的距离,track 是轨迹,p 是定值,_crv是轨迹信息,同样使用aes加密
2.轨迹生成可以采集一条正常的,手动滑出来的轨迹,然后根据识别出的实际距离和样本轨迹中的距离相比,得到一个比值,然后将样本中的 x 值和时间值都做一个对应的缩放,生成新的轨迹,将之前的缺口位置加入参与计算
1 | |
3.最后生成轨迹和缺口位置以及上诉的iv值进行aes加密,就得到checkInfoTp接口的请求参数data
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Spider Blog!