jd app ep和sign参数获取解析
jd app ep和sign参数获取解析
版本:v11.6.4
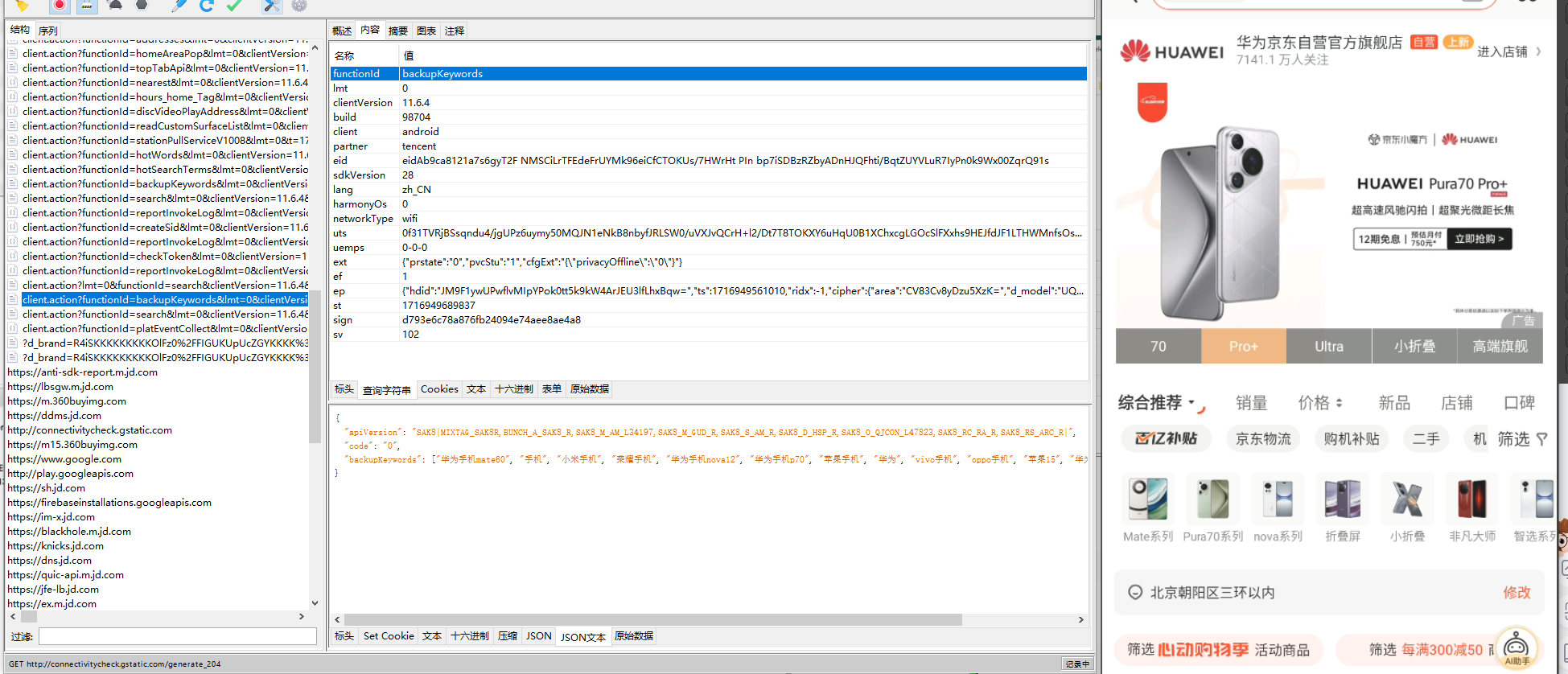
GET中传递的参数:
- functionId,
"functionId": "backupKeywords" - ep,需逆向
- sign,需逆向
- st,看似时间戳
- sv,看似固定值
- eid,删除后不影响(忽略)
“ep”:
1 | |
拦截器
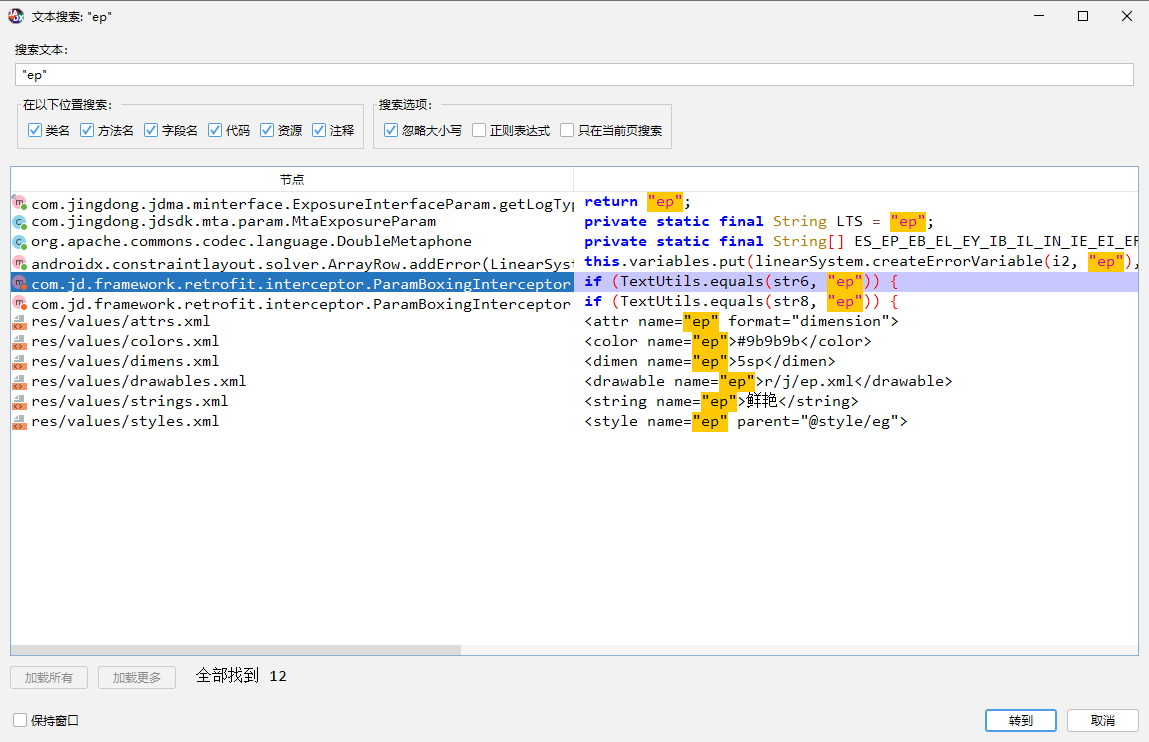
builder.addEncodedQueryParameter(str6, urlParams4.get(str6))
Map<String, String> urlParams4 = getUrlParams(str4)
这里应该就是将url的参数转换成字典,而ep就是从字典里面取值,str4里面就是完整的url链接
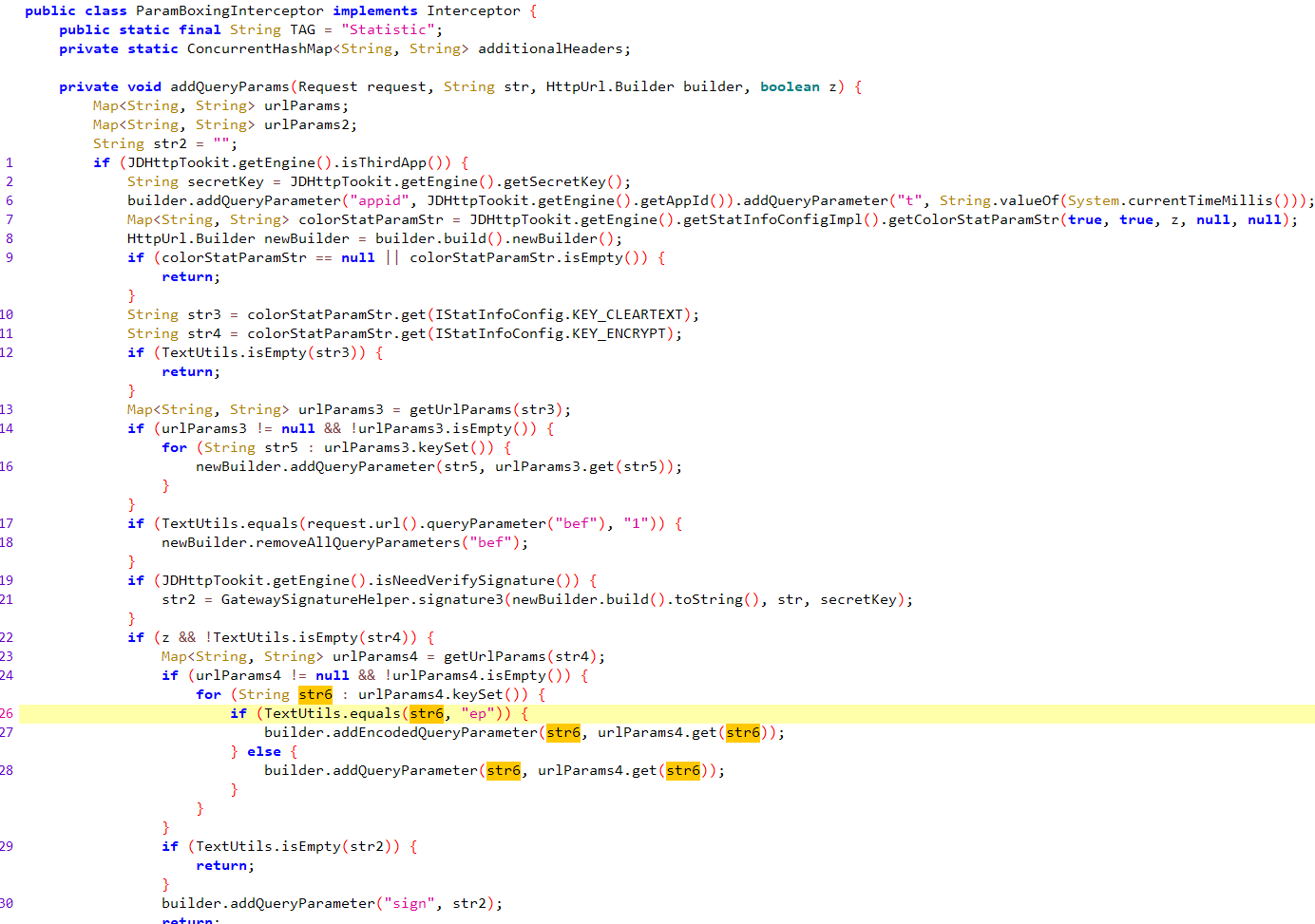
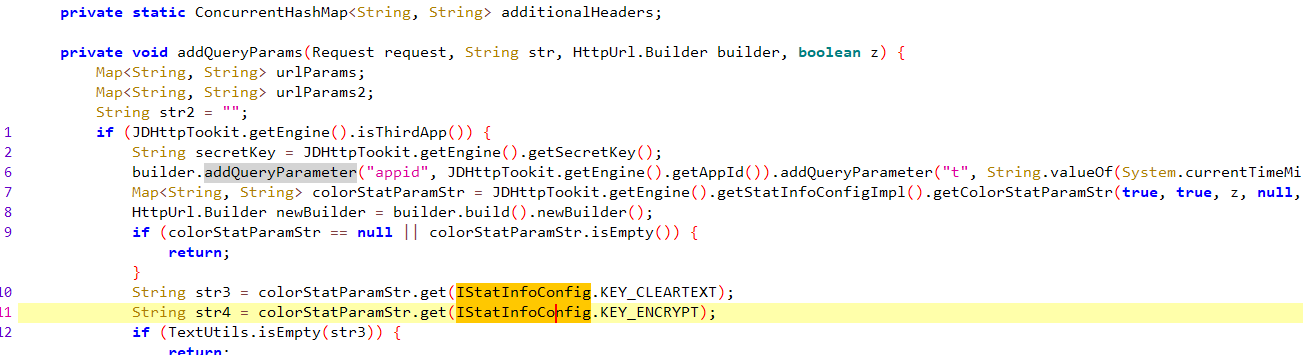
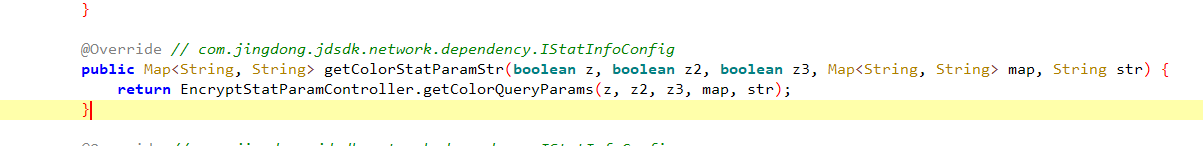
str4 就是从colorStatParamStr 中取出 “encrypt”
colorStatParamStr = JDHttpTookit.getEngine().getStatInfoConfigImpl().getColorStatParamStr(true, true, z, null, null);
colorStatParamStr 是个接口,我们需要找到谁实现了这个接口
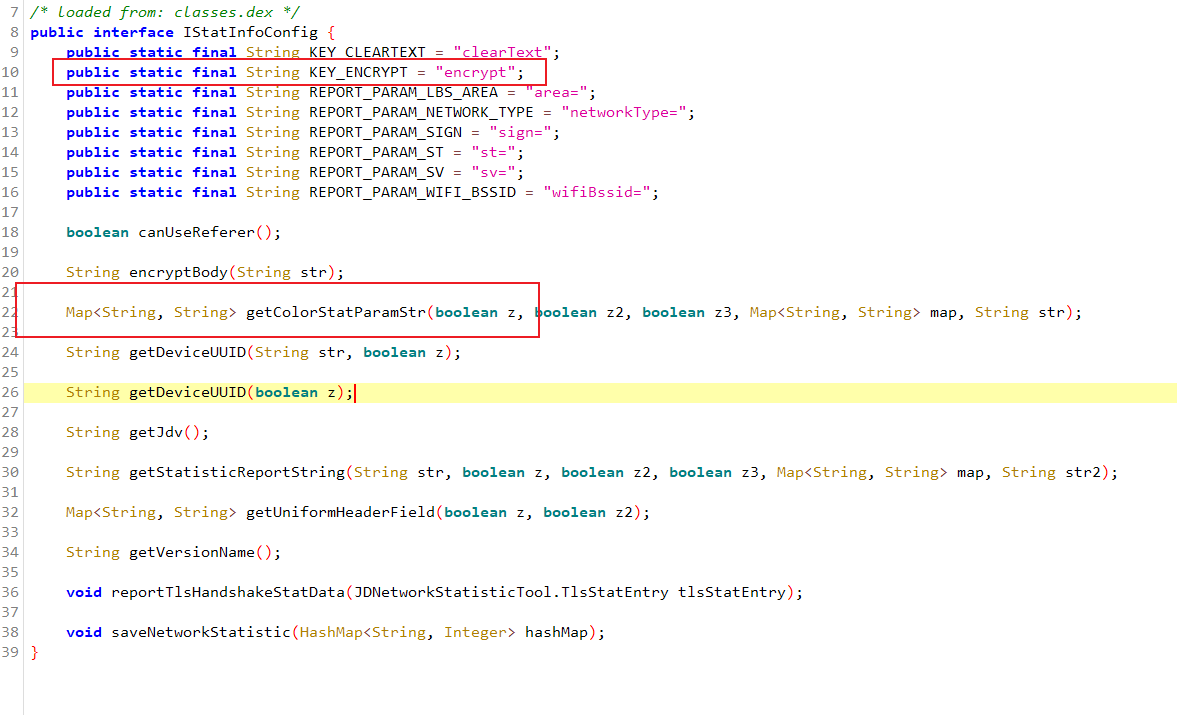
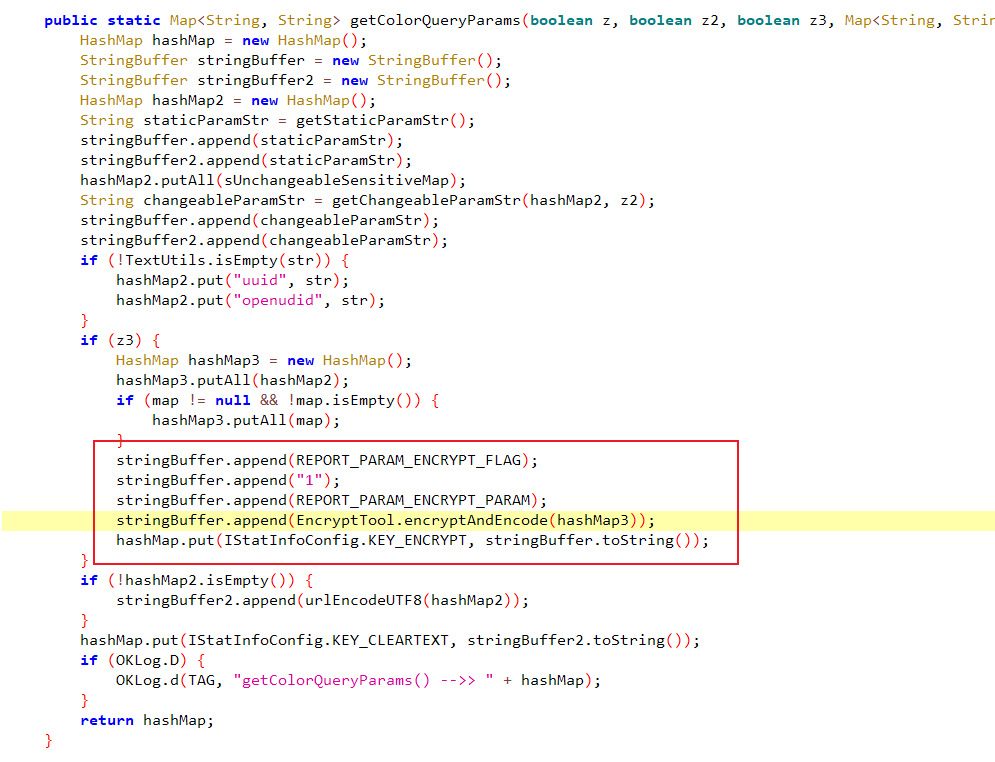
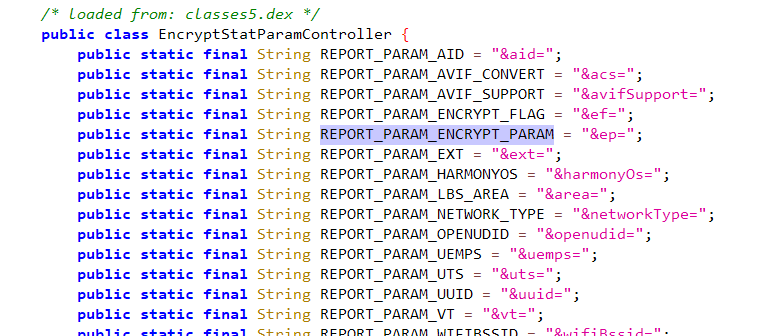
REPORT_PARAM_ENCRYPT_PARAM 里面能看到这里做了很多拼接
重点主要是看 EncryptTool.encryptAndEncode(hashMap3)
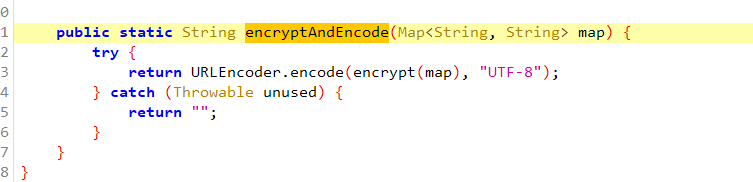
可以hook一下 encryptAndEncode 这个方法,encrypt 方法也在上面,这里应该是反编译出了问题,这里做了个缓存,判断如果有缓存取缓存,没有缓存就去取 r2.b(r7, r6) , r2 是 com.jd.phc.e.d 方法的返回值,那我们取看一下 com.jd.phc.e 里面是什么
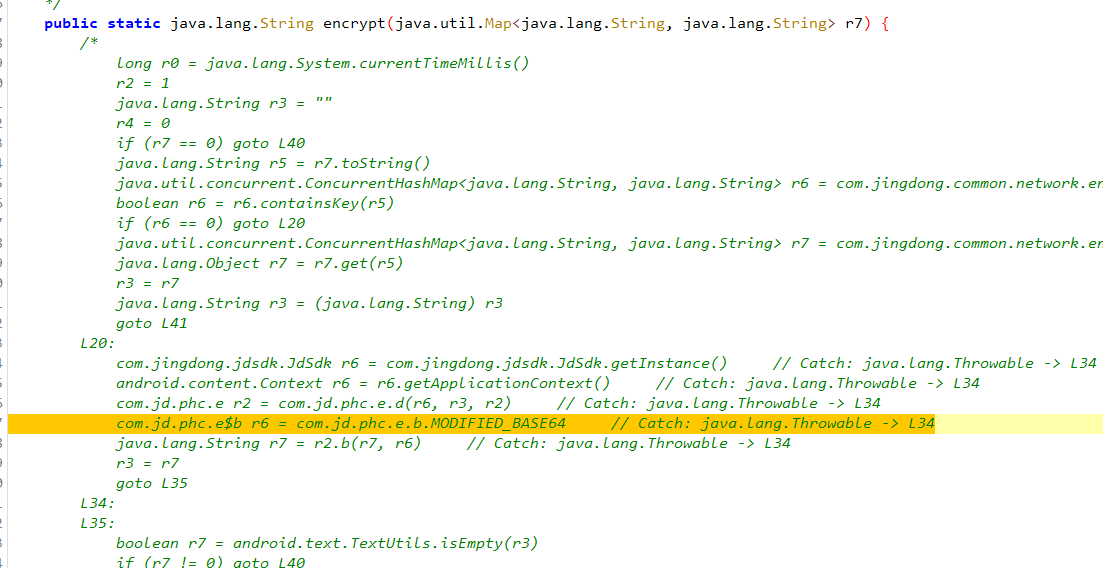
这里面应该就是专门的一个加密库
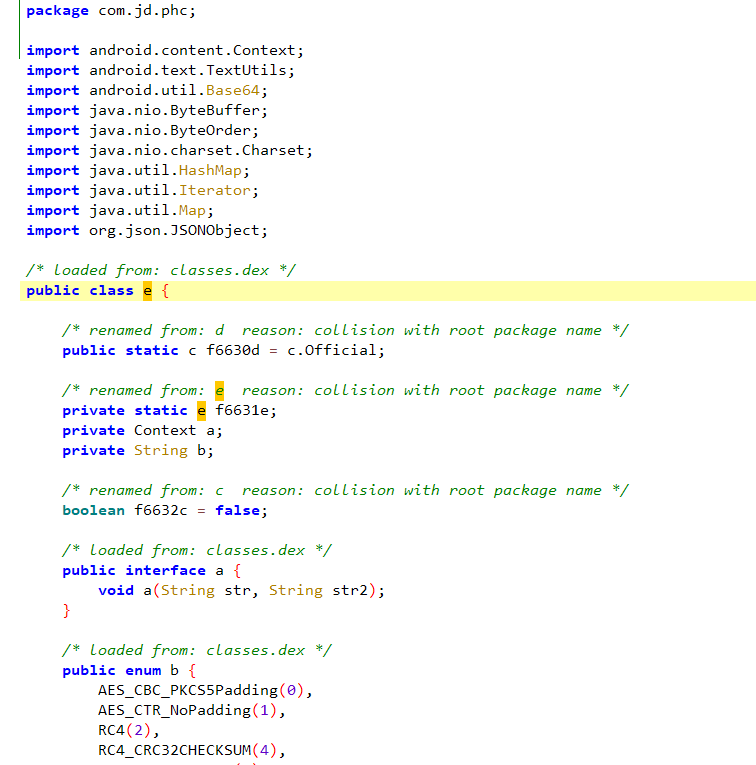
下面就是r2.b方法,里面返回的就是ep参数里面的值
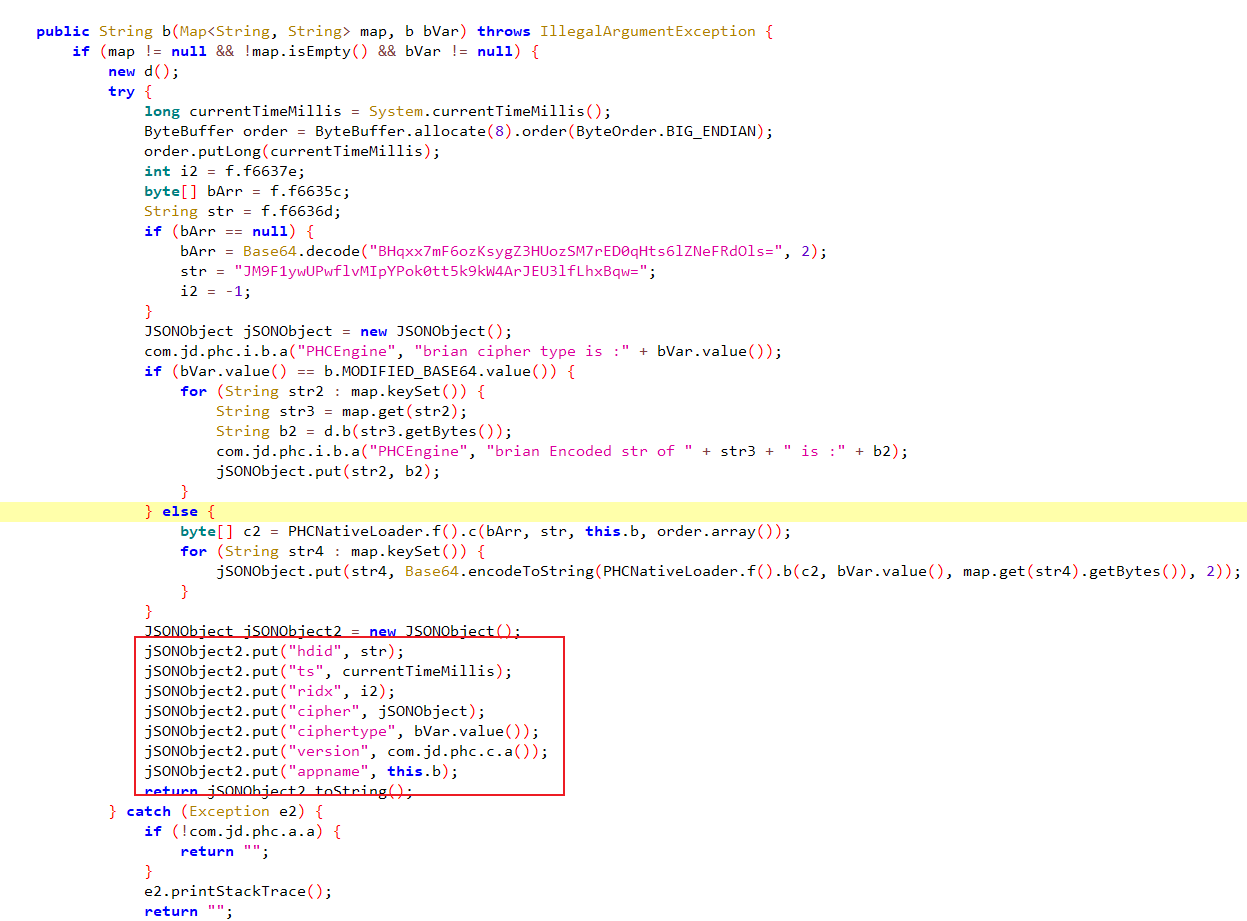
可以看到,出了时间戳 currentTimeMillis 和 cipher 以外,其他的都是固定值,所以这里我们要看的只有 cipher,cipher里面有很多参数
1 | |
搜先我们需要知道,传进来的map值是什么,以及 里面的d.b对value做了什么处理
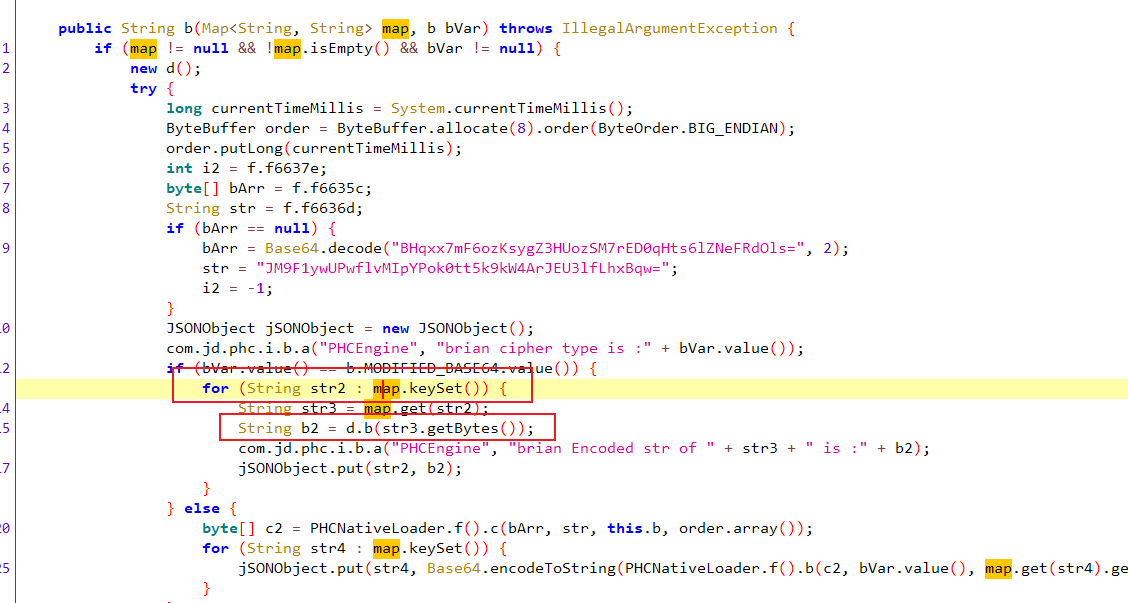
我们可以通过hook前面的 encryptAndEncode 方法,查看传入的map值是什么
1 | |
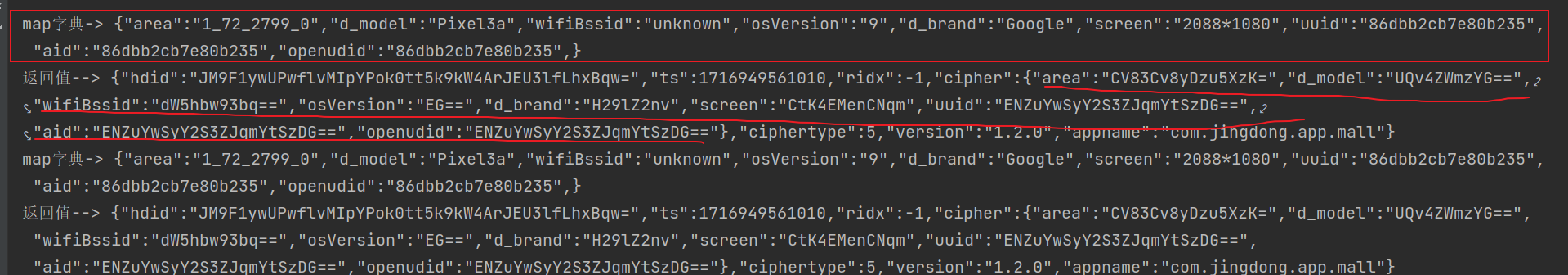
可以看到传入的是一些设备信息,而cipher是对这些设备信息做了类似于base64的加密
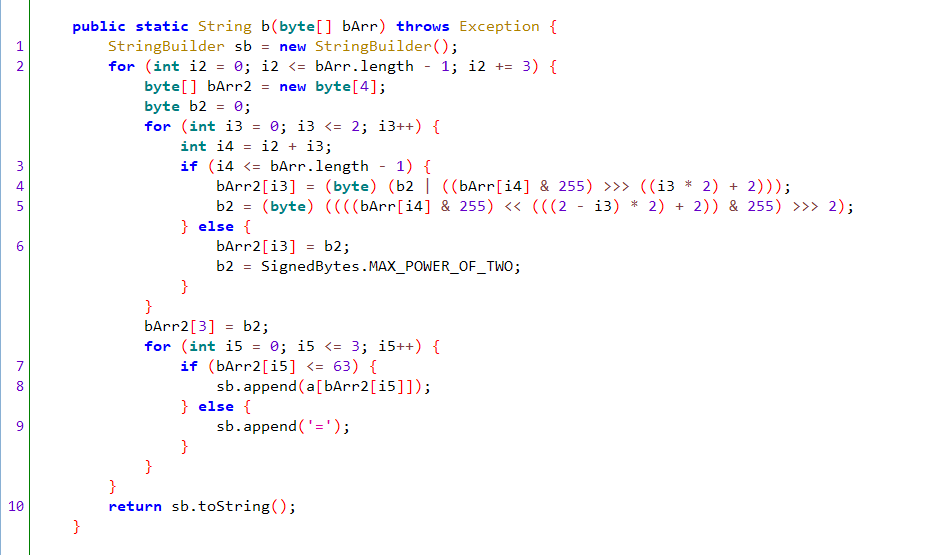
d.b方法,需要将其转换成python代码
1 | |
运行结果也没有问题
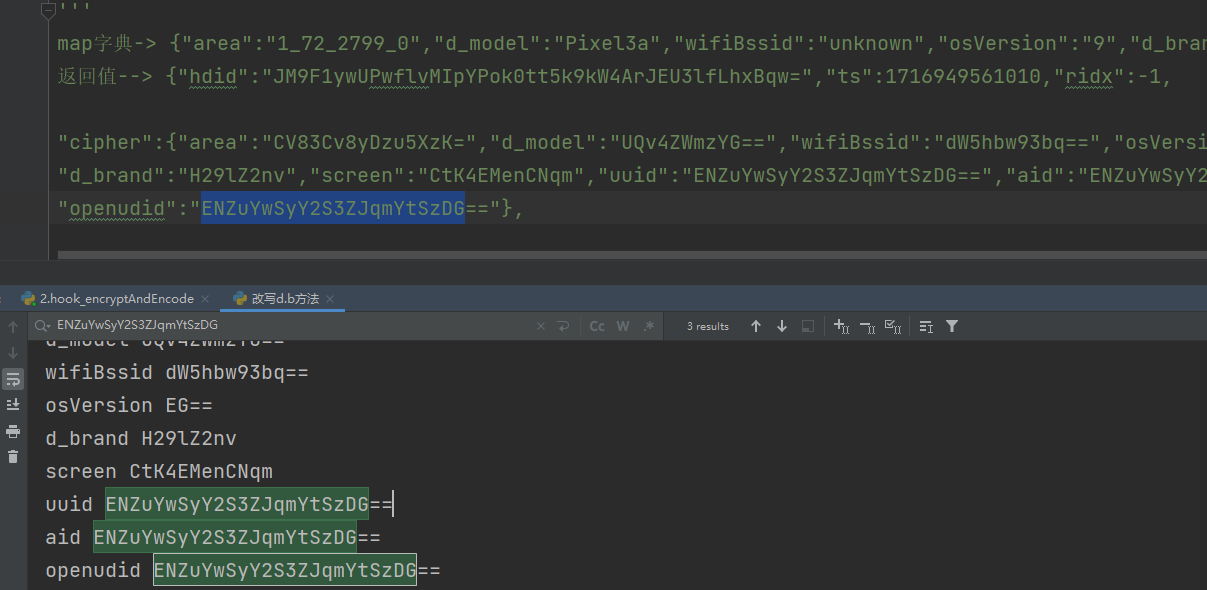
最后我们可以拼接ep参数,其中uuid aid open_udid 值相同,可以通过随机数随机生成,固定也可以
1 | |
sign
如果通过关键字搜索的话,会有很多结果 如果要一个个看的话,会很耗时间,这里可以使用看调用栈的方式去找,通过抓包可以发现基本上每个请求都会携带sign, 而我们前面hook encryptAndEncode 的時候,也順便打印了调用栈,那我们可以去找一下这几个调用栈看下有没有有用的地方
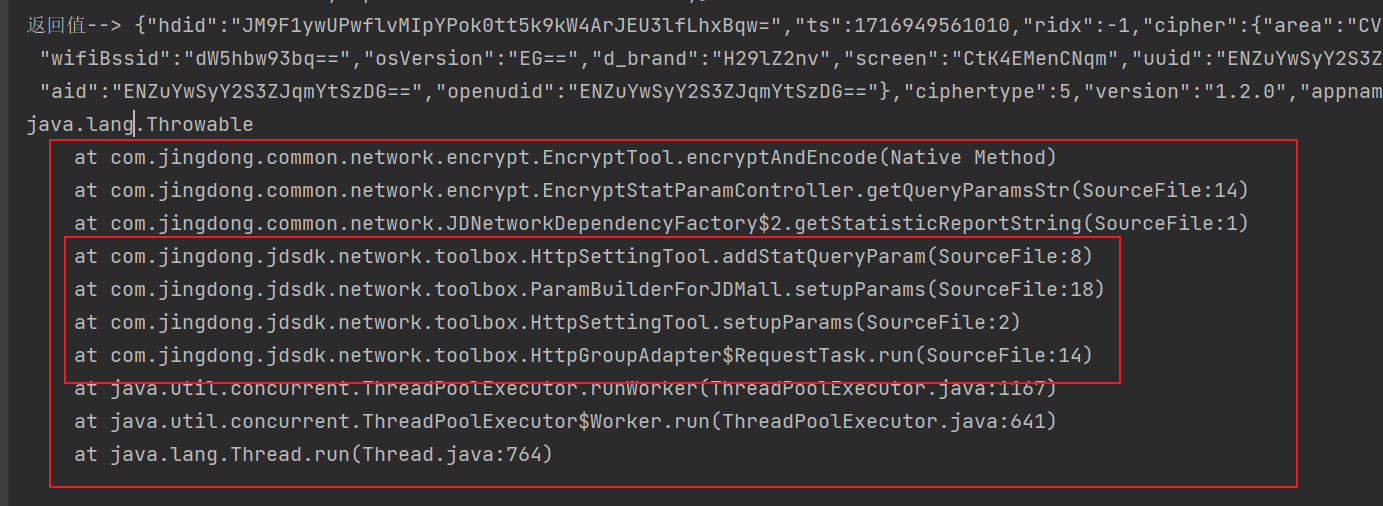
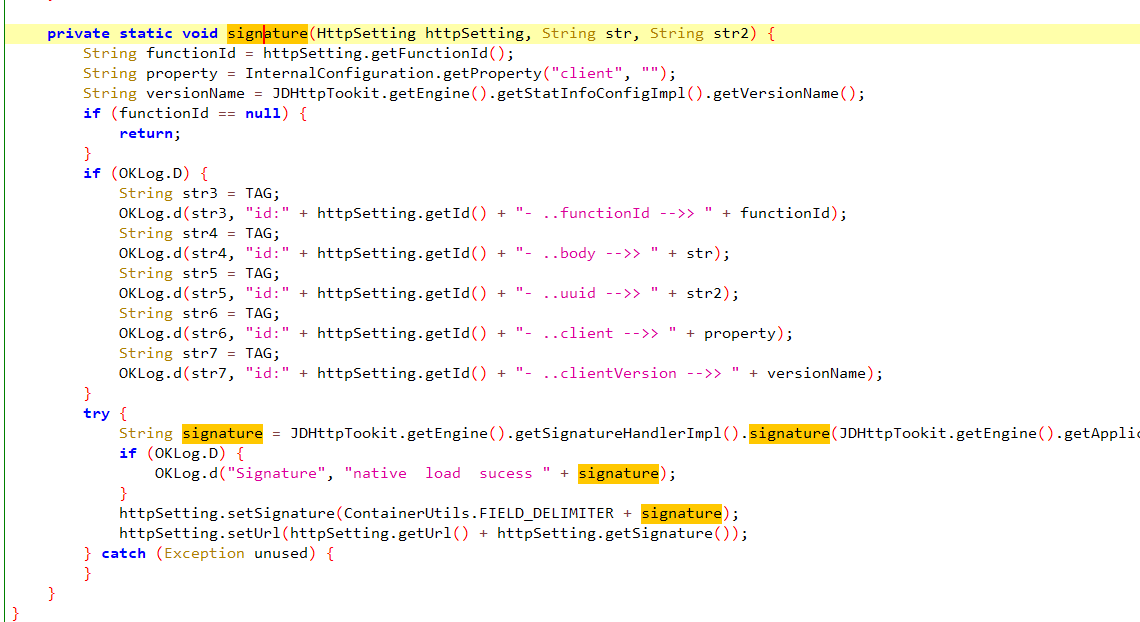
在 com.jingdong.jdsdk.network.toolbox.ParamBuilderForJDMall.setupParams 里面 能看到有一个 signature 方法
1 | |
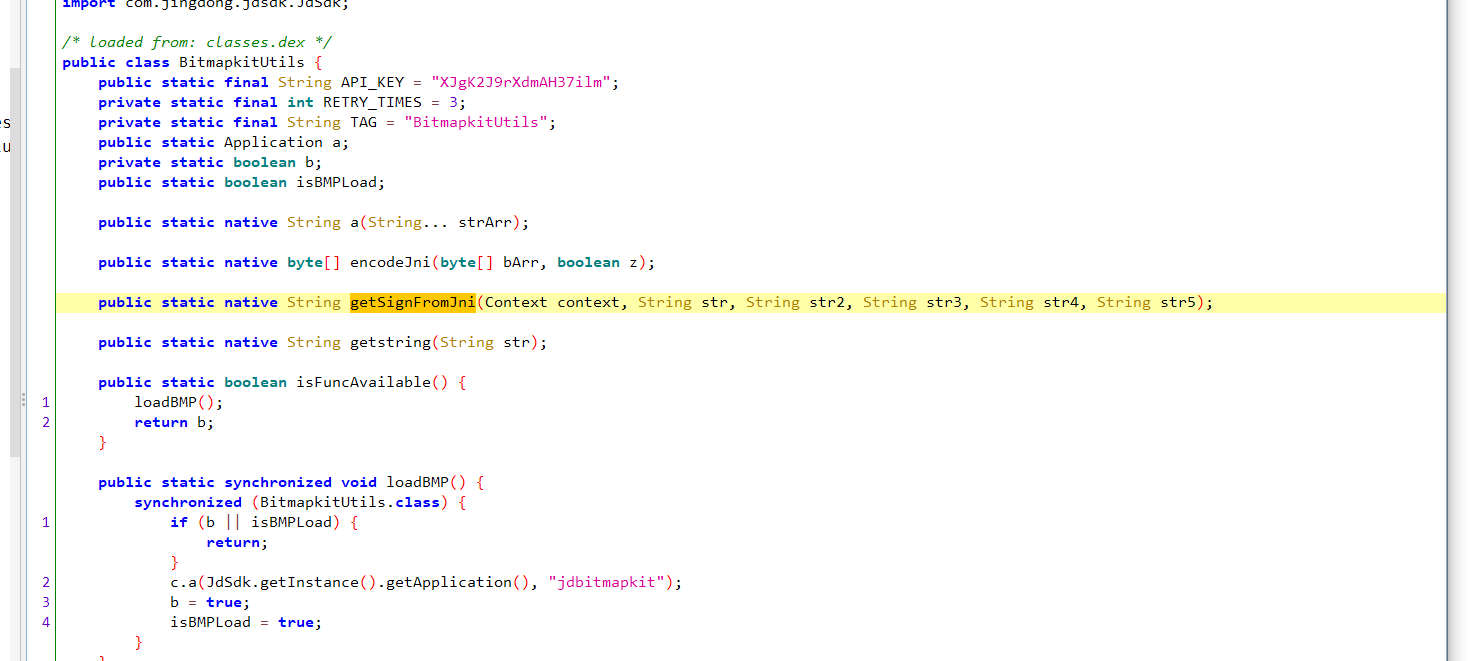
我们再看下这个 getSignatureHandlerImpl().signature 方法,这里也是一个接口,通过查找用例 可以看到这里有个 getSignFromJni 方法,点进去看一下
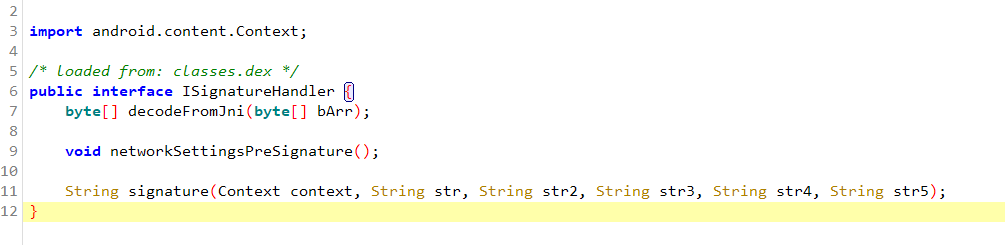
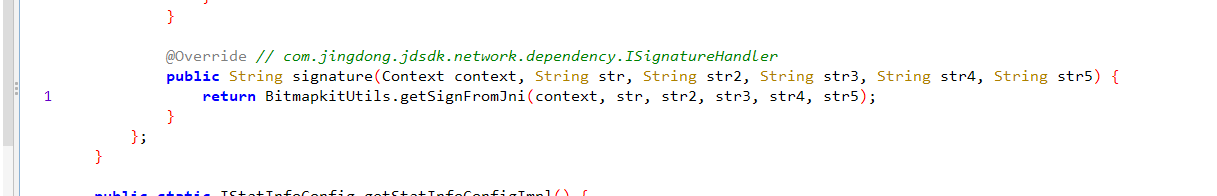
可以发现这里就是native层加密了,可以hook一下这个 getSignFromJni 方法看一下对不对,我们用ida打开 jdbitmapkit 这个so文件看一下
1 | |
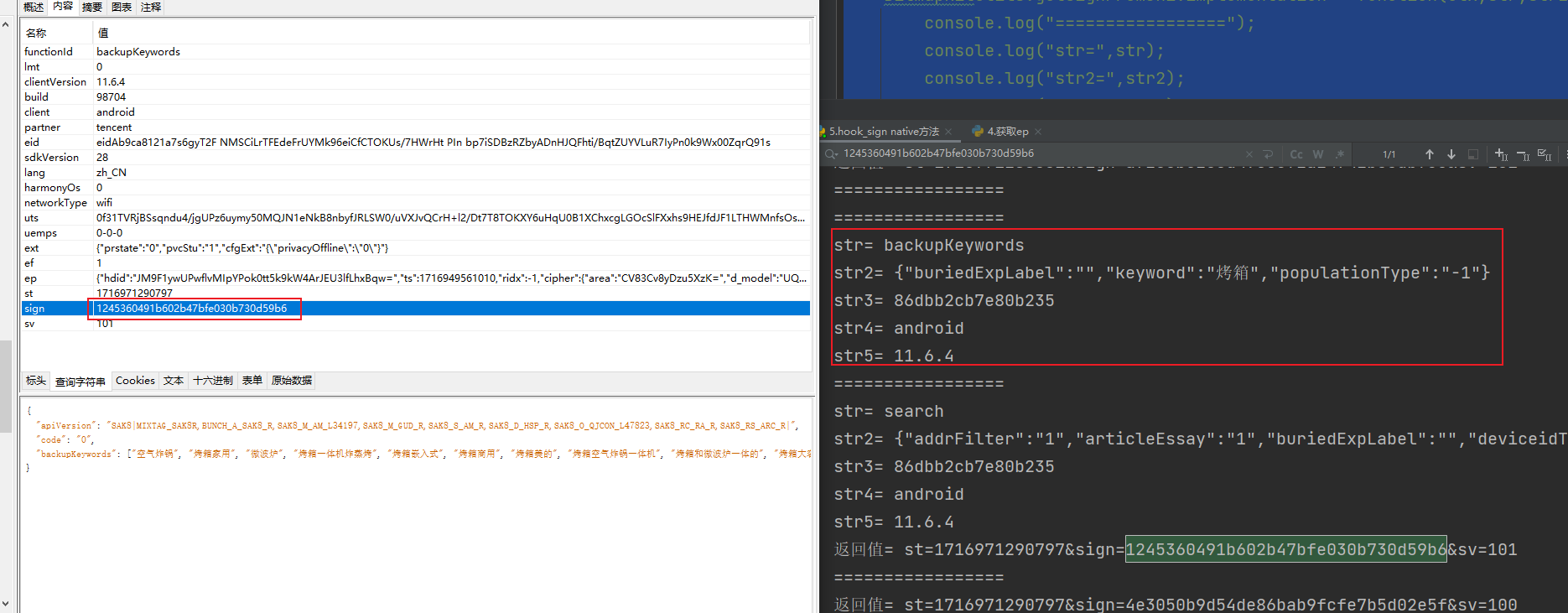
运行看一下,和抓包的结果是一样的,里面的参数就是这几个
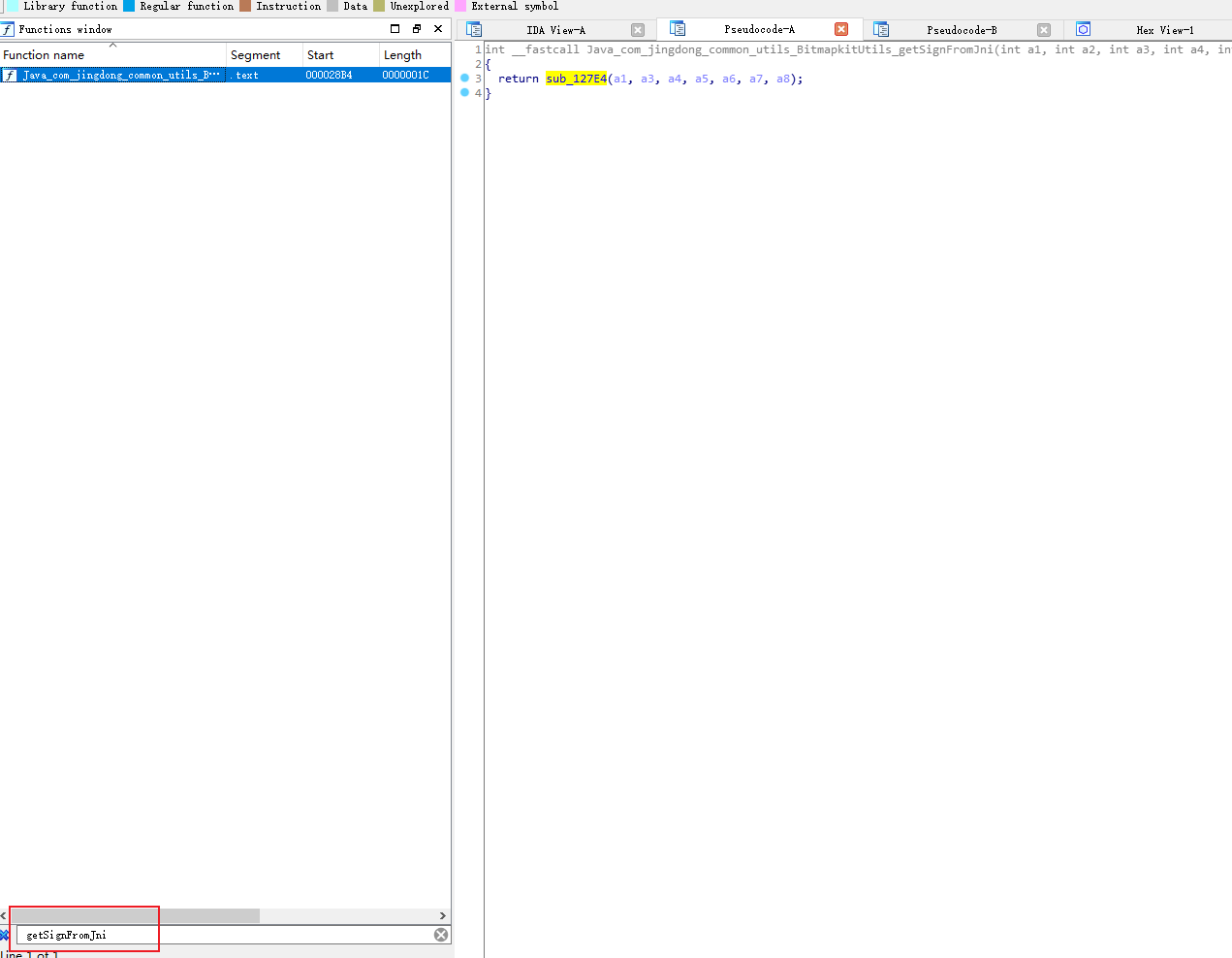
打开ida后,搜索 getSignFromJni 可以看到这是一个静态方法
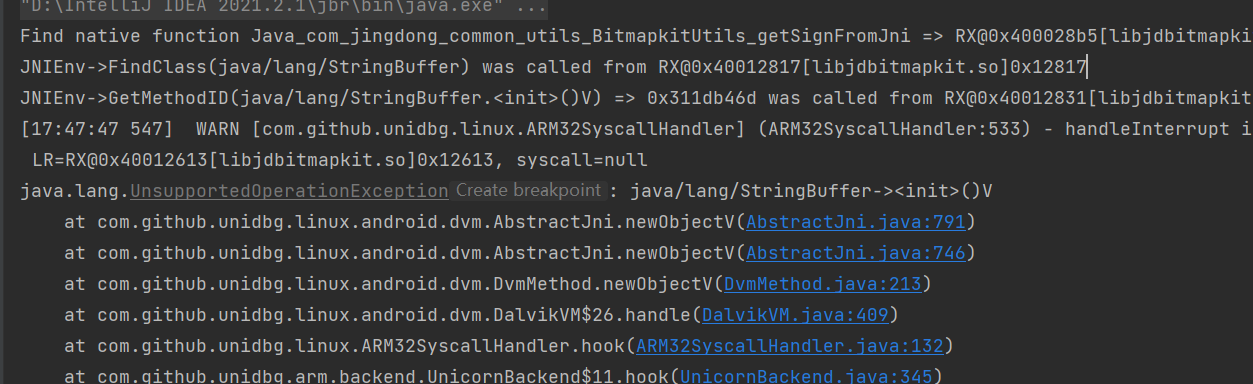
我们用unidbg模拟设备去主动调用c中的函数,
1 | |
不出意外的报错,接下来就是补环境了
1 | |
环境补齐后,看下运行结果,成功取到值,搜索关键字那里只需要留一个 keyword 就好
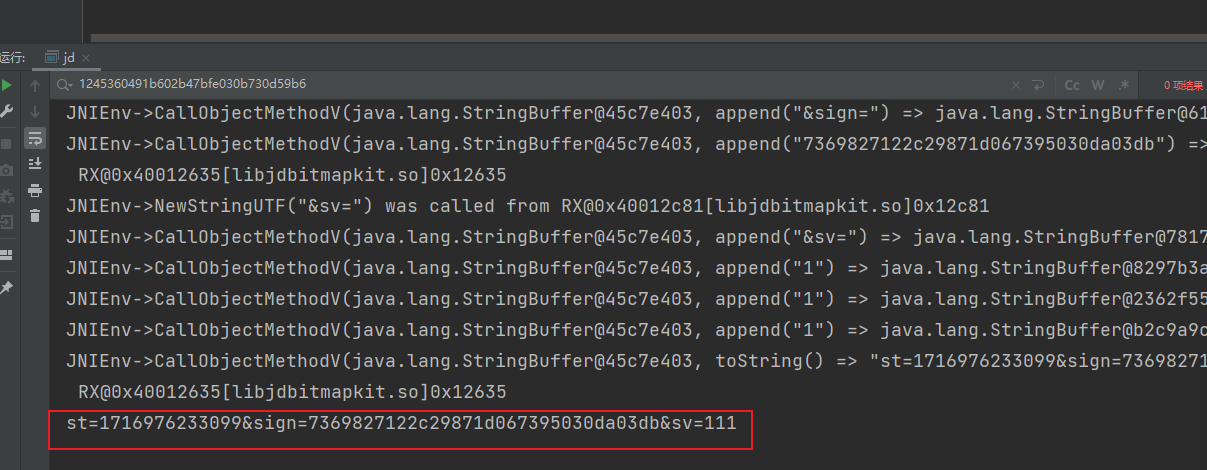
因为要打包给py调用,所以这里需要加上证书以及加上参数传递,完整代码如下
1 | |
打包成jar包后,我们在用python调用试一下,发现能获得结果,那就没有问题
1 | |
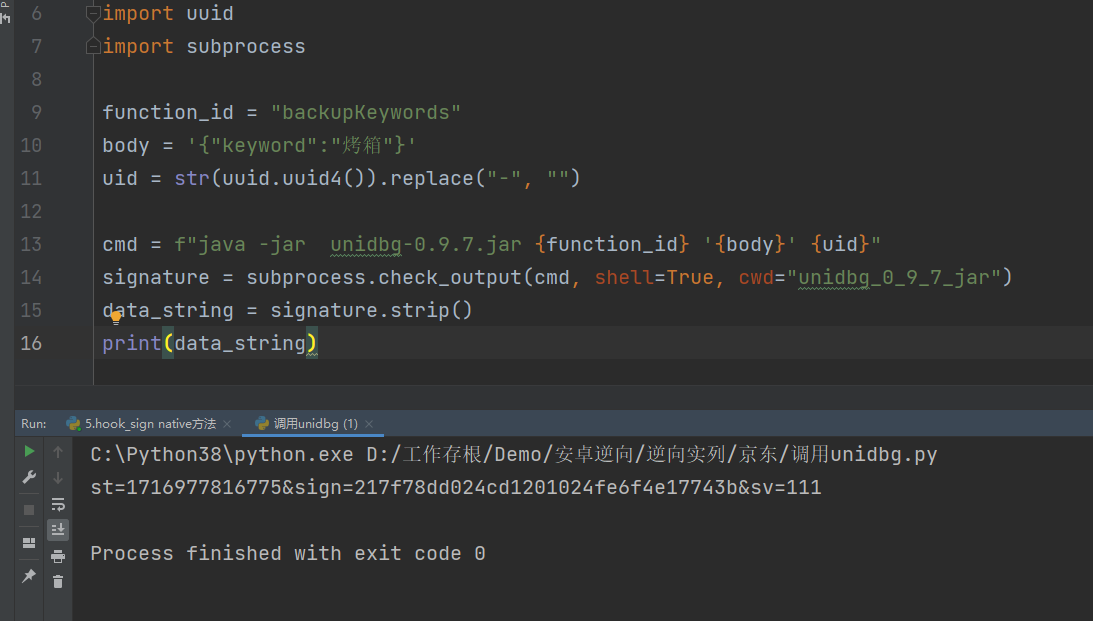
代码整合
最后整理一下代码,因为unidbg对windows的支持问题,会导致sign的值无法通过校验,需要在linux或者ubuntu环境中运行
1 | |